If you want to reverse engineer .net applications (or any application for that matter), you'll have to try different types of weapons from your arsenal. There are no 'N steps to reverse engineer a .net application' kind of thing. Each application vendor may use their best known method of securing their code. And you'll have to think out-of-box to get to know the internals of an application. What you can do instead is to know about the right tools needed to accomplish your task. There may be various reasons of why you wish to reverse engineer a .net app. Some may be legal ones, such as you may wish to find out the behavior of a old dll library of which you don't have the code right now and you may be looking to fix the bugs. Other may be illegal ones, like patching an application to convert it from trial version to full version. (BTW, it's called **illegal **for a reason. Always purchase legal software licenses from trusted vendors. Not only it's safe and ethical, it'll add a lot of value to your overall workflow. Remember, you don't get anything for FREE in this world. There is always somebody else's gain when something is being offered for FREE).
7 Must Have Tools to Reverse Engineer .NET applications
So what are those tools. Here are the 7 tools that I think should help you analyze and change most aspects of your application. 1. CFFExplorer: The tool is awesome for analyzing the hex code of your application. It gives you various parameters related to an assembly including but not limited to Address Converter, Hex Editor, Meta data editor, PE Header Rebuilder etc. You can analyze the hex codes and modify the data in the assembly to create patches. 2. Fiddler / Wireshark: Telerik Fiddler and Wireshark are must have tools for analyzing the network protocols and TCP/IP traffic to and fro your computer. These tools analyze and capture each and every packet that passes through your network interface card. With these tools, you can track the communication that an application is doing with the outside world. You can check what kind of information from your computer, a particular app is sending home.
2. Fiddler / Wireshark: Telerik Fiddler and Wireshark are must have tools for analyzing the network protocols and TCP/IP traffic to and fro your computer. These tools analyze and capture each and every packet that passes through your network interface card. With these tools, you can track the communication that an application is doing with the outside world. You can check what kind of information from your computer, a particular app is sending home. 3. Process Monitor: This tool by Microsoft Technet is a perfect one for tracking the behavior of an application. You can monitor the tasks being performed by an application during it's execution time. It tracks Registry Access, File System Access, Network Access, Thread Management etc. You can also create filters to only track the things that you wish to track and bypass the unnecessary captures.
3. Process Monitor: This tool by Microsoft Technet is a perfect one for tracking the behavior of an application. You can monitor the tasks being performed by an application during it's execution time. It tracks Registry Access, File System Access, Network Access, Thread Management etc. You can also create filters to only track the things that you wish to track and bypass the unnecessary captures. 4. Mega Dumper: The tool helps you the dump the entire application as it's present in the memory to your file system for analysis. It dumps all the referenced files as well. So you have your entire application dumped to your harddisk in the format being executed by the .net CLR.
4. Mega Dumper: The tool helps you the dump the entire application as it's present in the memory to your file system for analysis. It dumps all the referenced files as well. So you have your entire application dumped to your harddisk in the format being executed by the .net CLR.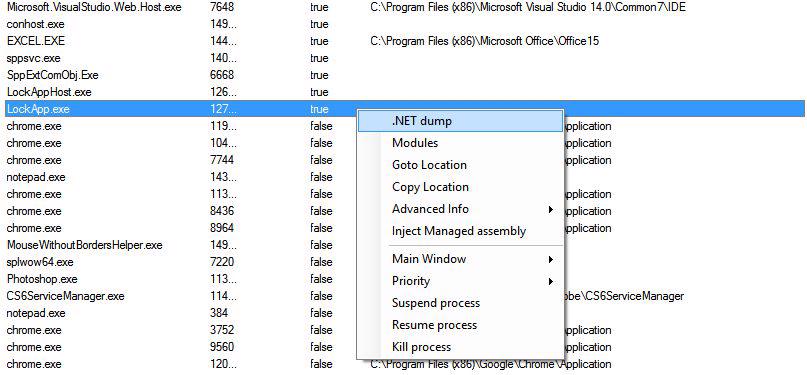 5. Registry Finder: Do you know there can be hidden registry keys in Windows Registry and the inbuilt regedit tool doesn't look in those keys. An application might be creating certain hidden keys to store some vital information. Registry finder provides advanced search filters to help you easily find those keys.
5. Registry Finder: Do you know there can be hidden registry keys in Windows Registry and the inbuilt regedit tool doesn't look in those keys. An application might be creating certain hidden keys to store some vital information. Registry finder provides advanced search filters to help you easily find those keys. 6. Telerik JustDecompiler / .NET Reflector: No doubt these are best tools for reading the MSIL of an assembly. They also help you find the address location of a particular function or variable. While .NET Reflector is a paid one, Telerik JustDecompile is available for FREE. These tools also offer extensions to unobfuscate an obfuscated assembly so you can analyze the application more closely.
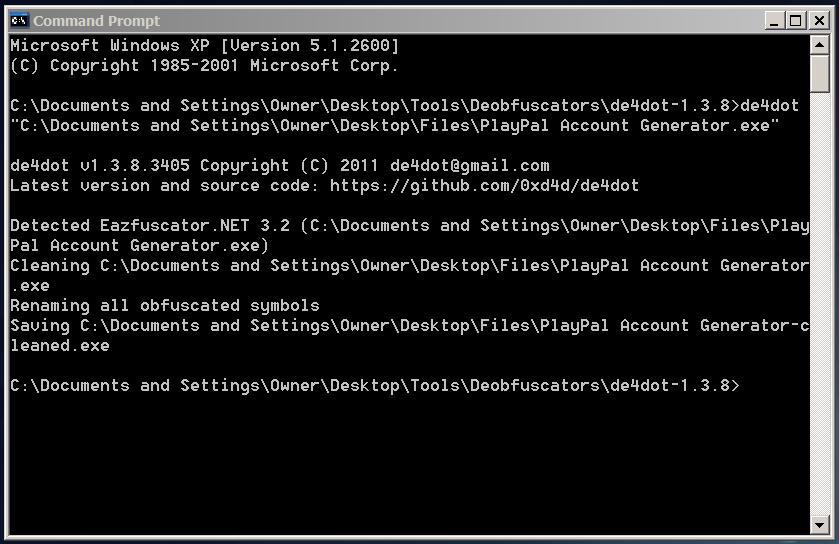
6. Telerik JustDecompiler / .NET Reflector: No doubt these are best tools for reading the MSIL of an assembly. They also help you find the address location of a particular function or variable. While .NET Reflector is a paid one, Telerik JustDecompile is available for FREE. These tools also offer extensions to unobfuscate an obfuscated assembly so you can analyze the application more closely.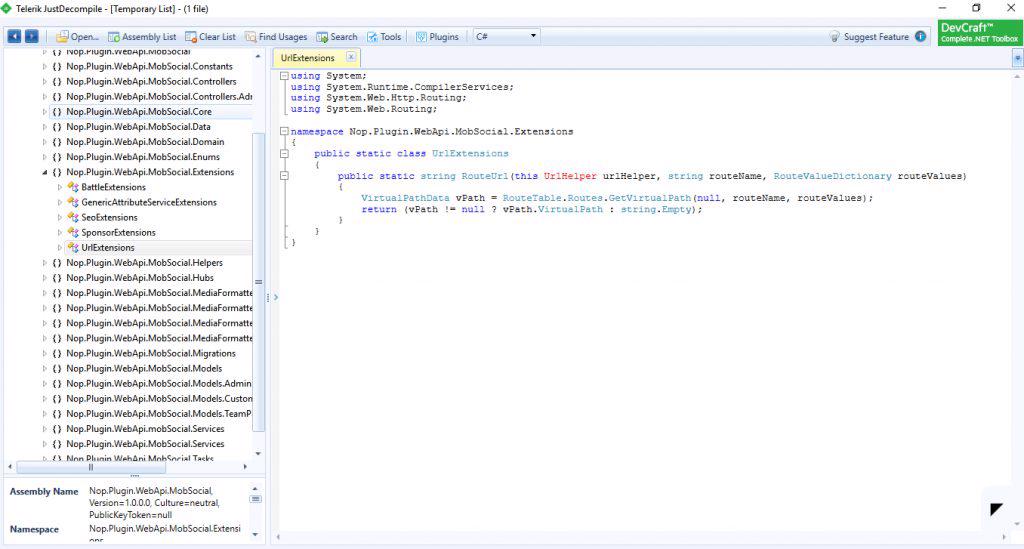 7. De4Dot: De4Dot is a perfect .NET application unpacker and deobfuscator. It's a command line tool and that's why it's powerful :D. It supports a wide variety of obfuscators including Dotfuscator, .NET Reactor, Smart Assembly etc. The tool helps to find the obfuscator used for packing the application and appropriately deobfuscates the application. The tool is also available as a plugin for Telerik Decompiler.
7. De4Dot: De4Dot is a perfect .NET application unpacker and deobfuscator. It's a command line tool and that's why it's powerful :D. It supports a wide variety of obfuscators including Dotfuscator, .NET Reactor, Smart Assembly etc. The tool helps to find the obfuscator used for packing the application and appropriately deobfuscates the application. The tool is also available as a plugin for Telerik Decompiler.